If You Don’t Know About These 3 Ways to Use Outlook 2016 More Efficiently, You’re Wasting Lots of Time
Microsoft Outlook is a professional email and calendar program that’s been used by businesses for over 15 years. It’s had many iterations over the years, but with 2016, and its integration with Office 365, Microsoft has taken Outlook to the next level. Today, small and medium-sized businesses that couldn’t afford the enterprise-level application can now benefit from Outlook 2016.
The following are 3 ways to help you use Outlook 2016 more efficiently.
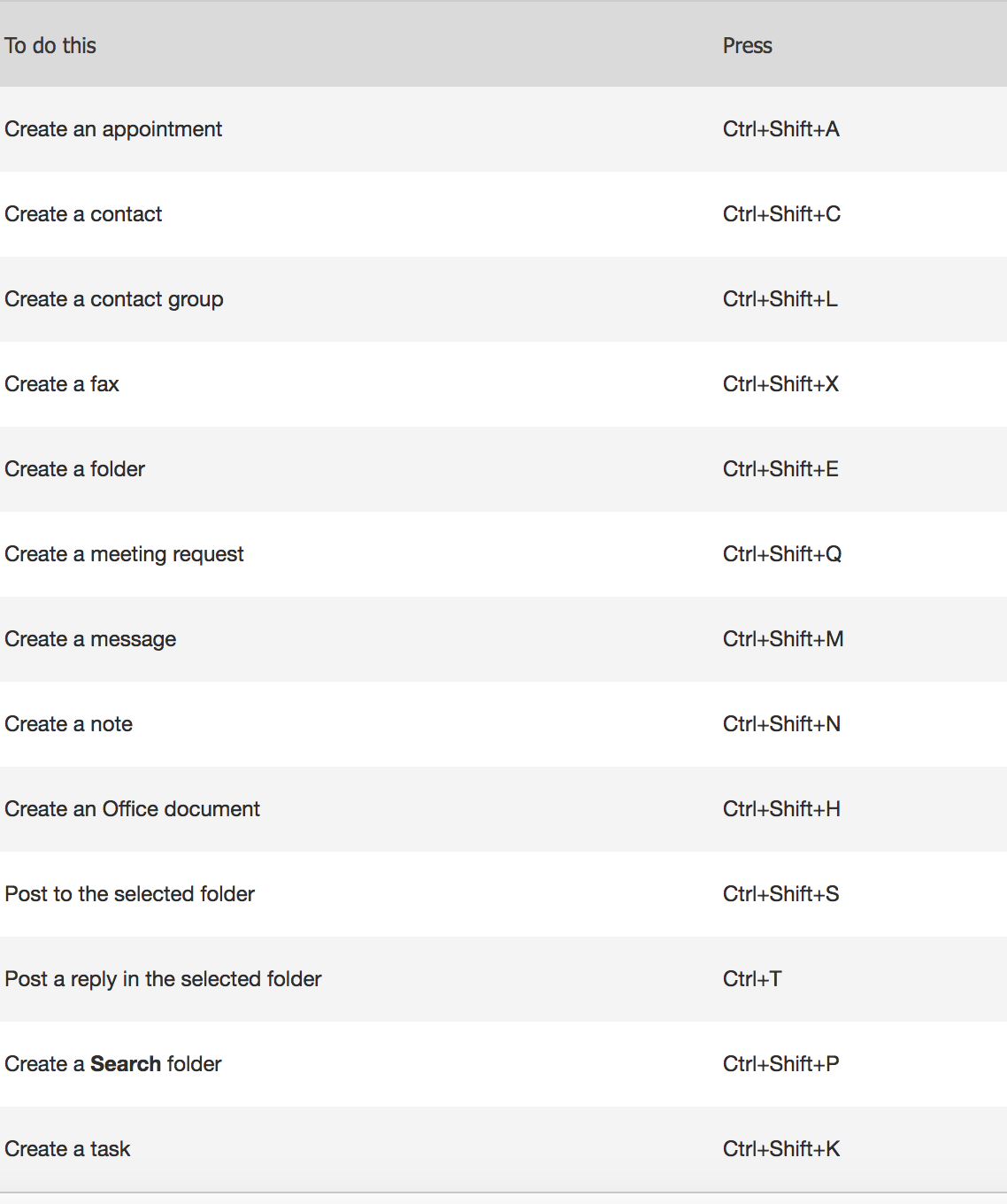
1. Keyboard Shortcuts
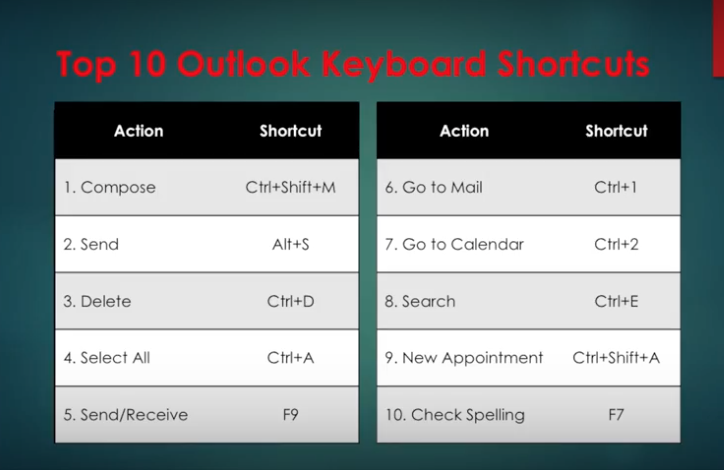
Using keyboard shortcuts in Outlook on Windows will help you work more efficiently. It’s also handy for those who have mobility or vision disabilities because using keyboard shortcuts can often be easier than using a touchscreen or mouse. Here are some popular keyboard shortcuts you should try.
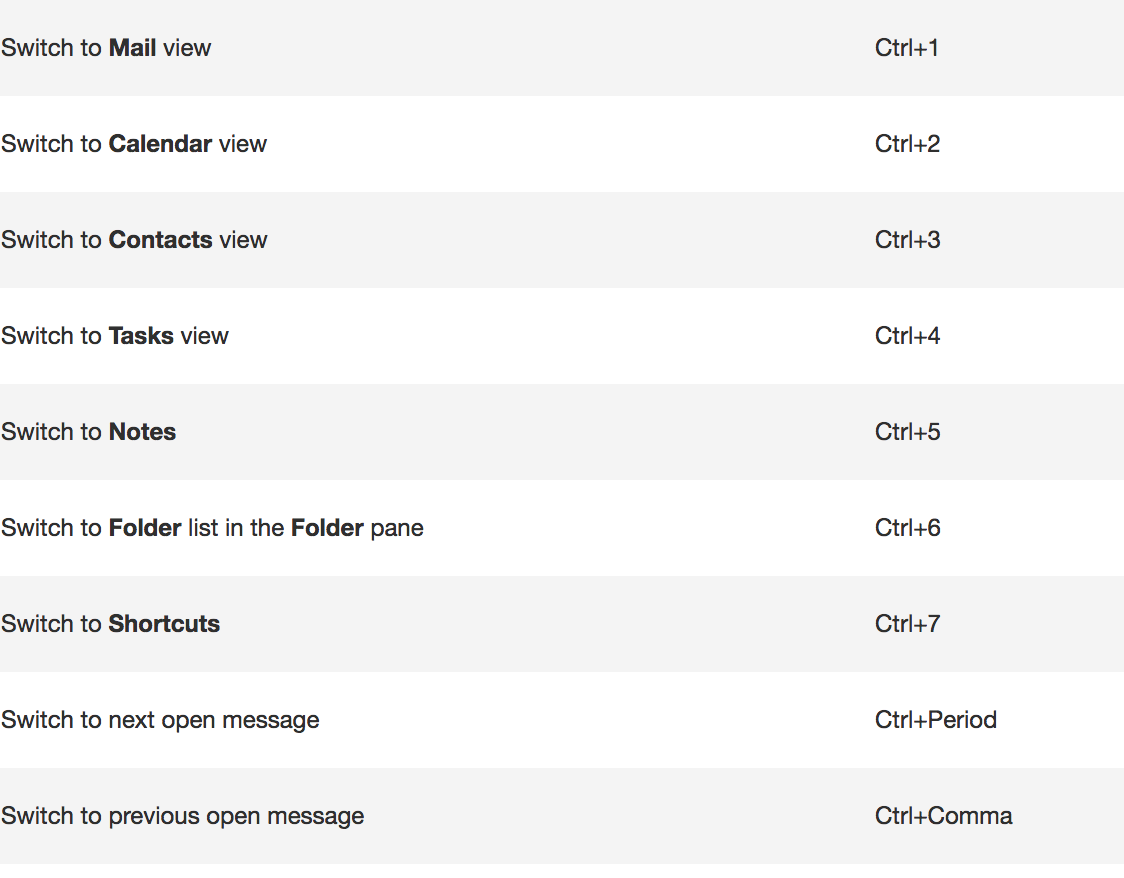
And there are more. Here are popular keyboard shortcuts for NAVIGATION:
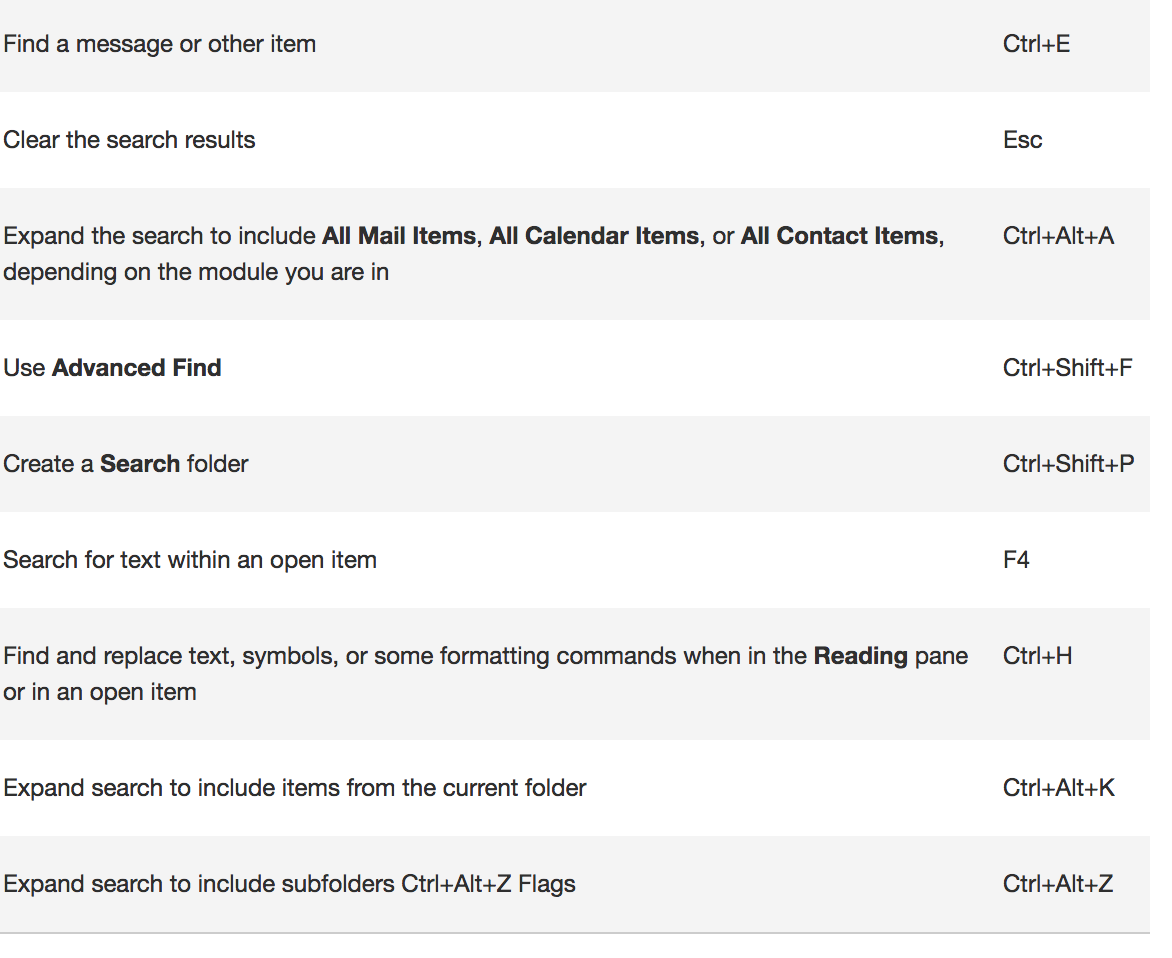
When searching, try these handy keyboard shortcuts:
To create an item or a file keep these shortcuts in mind.
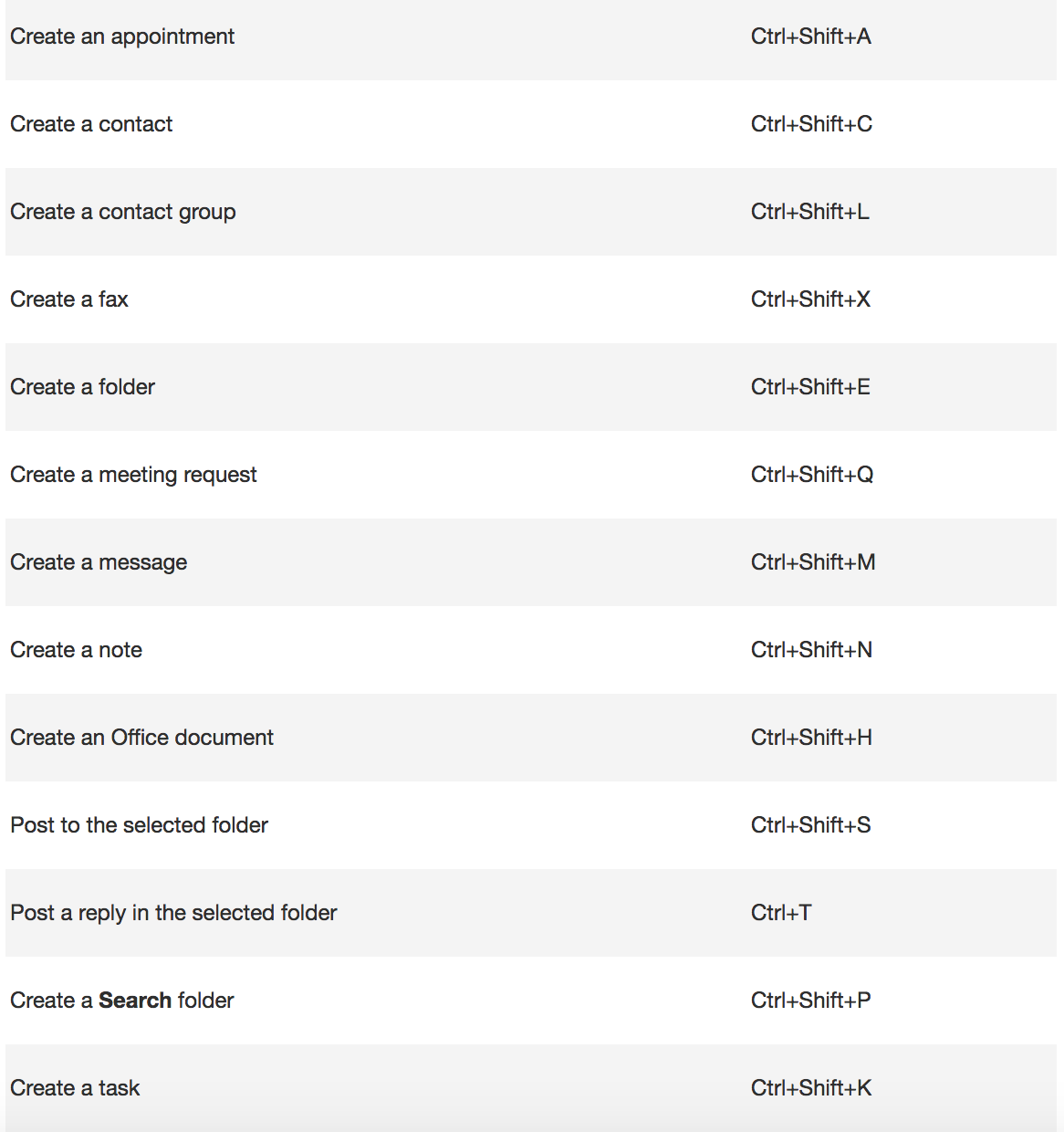
Shortcuts in Mail.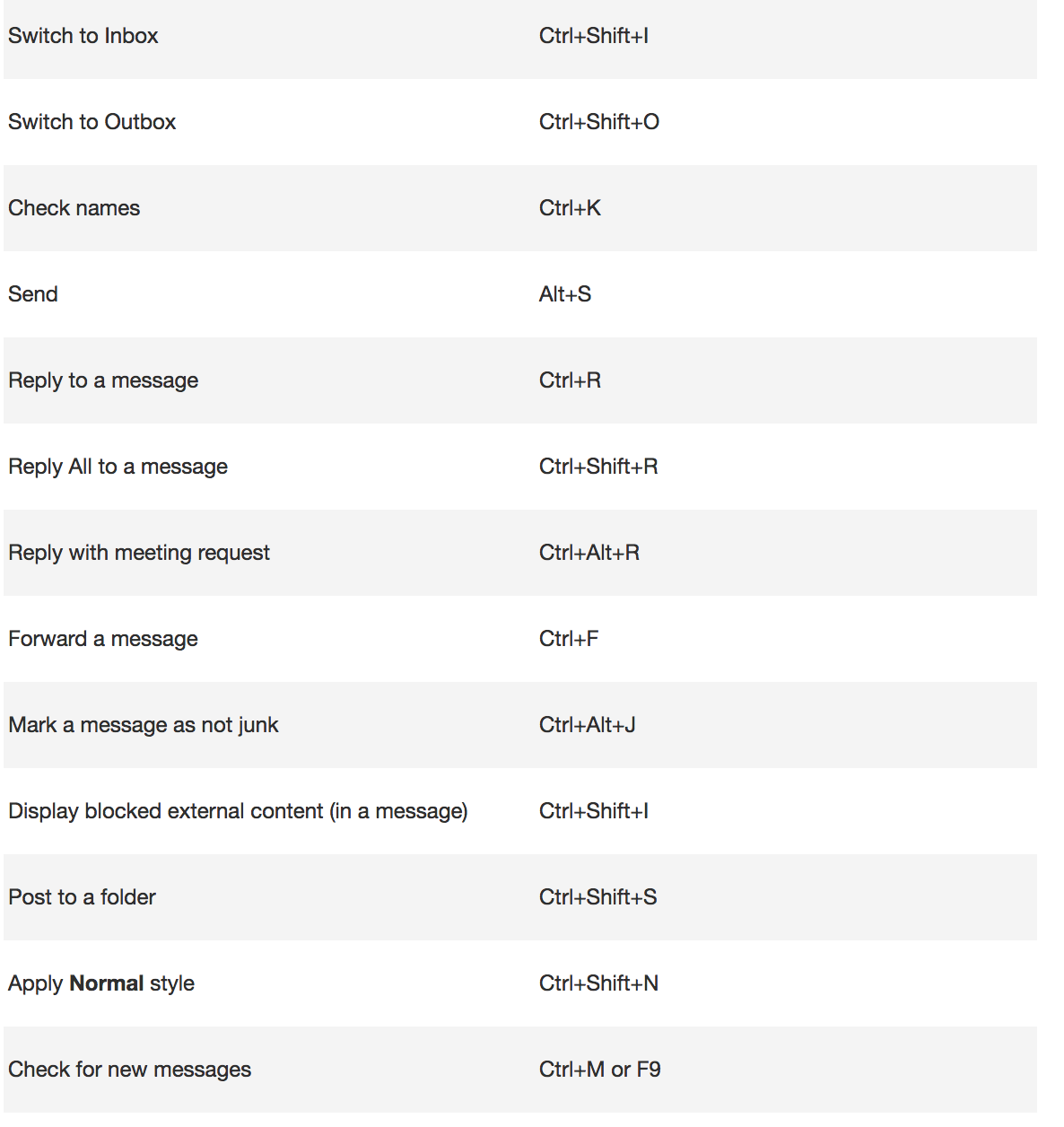
To see more Outlook 2016 Shortcuts go here.
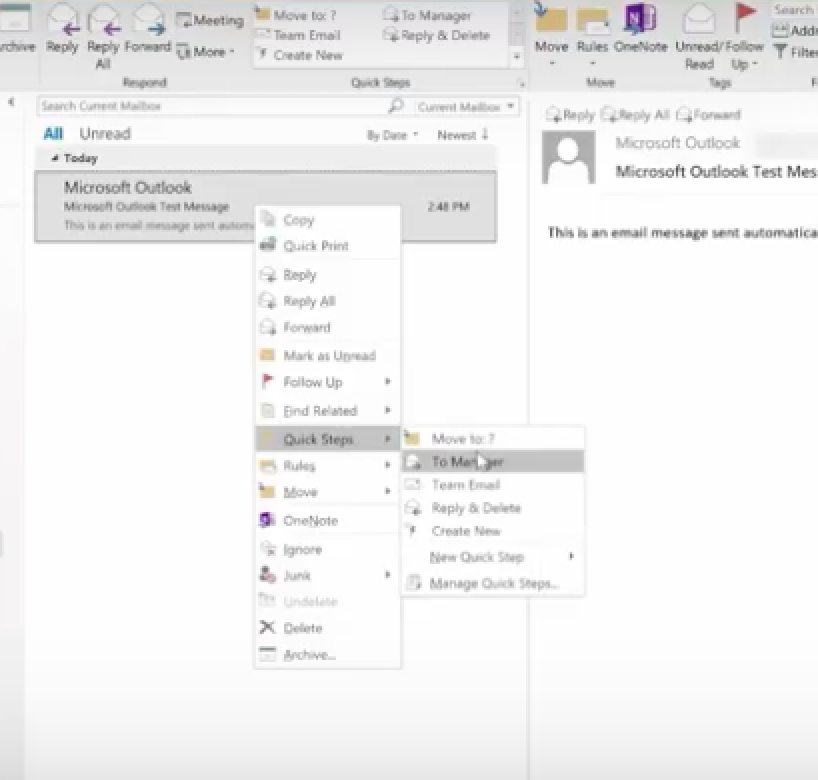
2. Use Quick Steps
Right-click any email, choose Quick Steps and choose from the list.
We’re going to choose Team Email. The first time we use this, Outlook asks you to name your team and enter their email addresses.
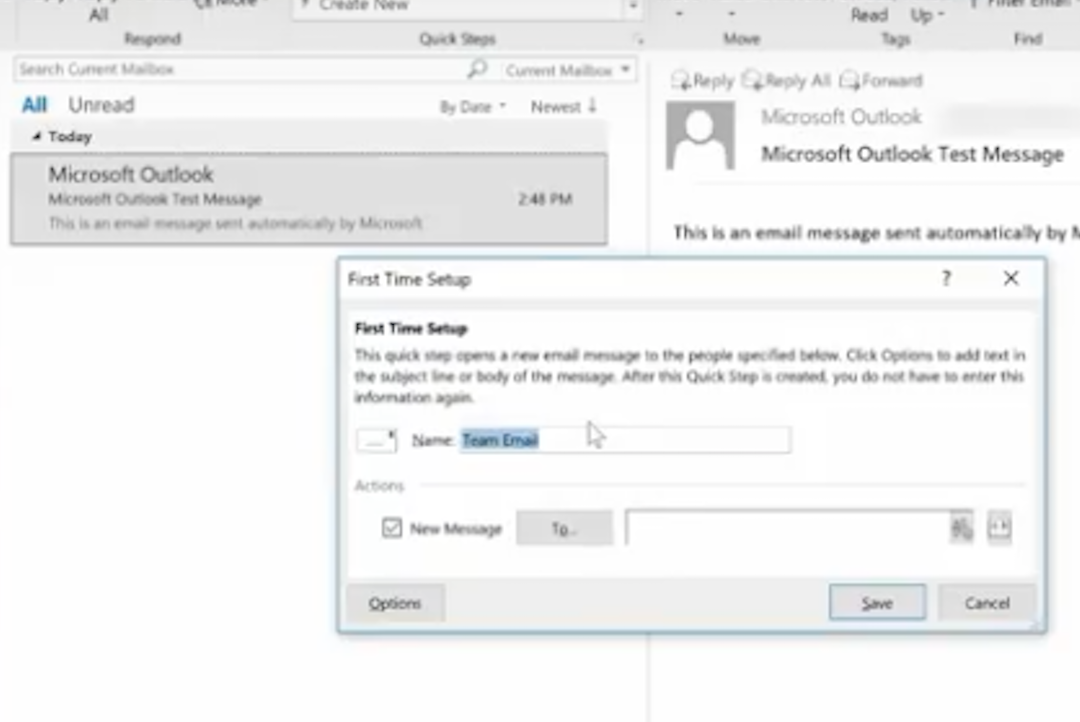
Then create a Keyboard Shortcut for this. So, the next time you hit Control Shift 1, an email to your entire team can be composed.
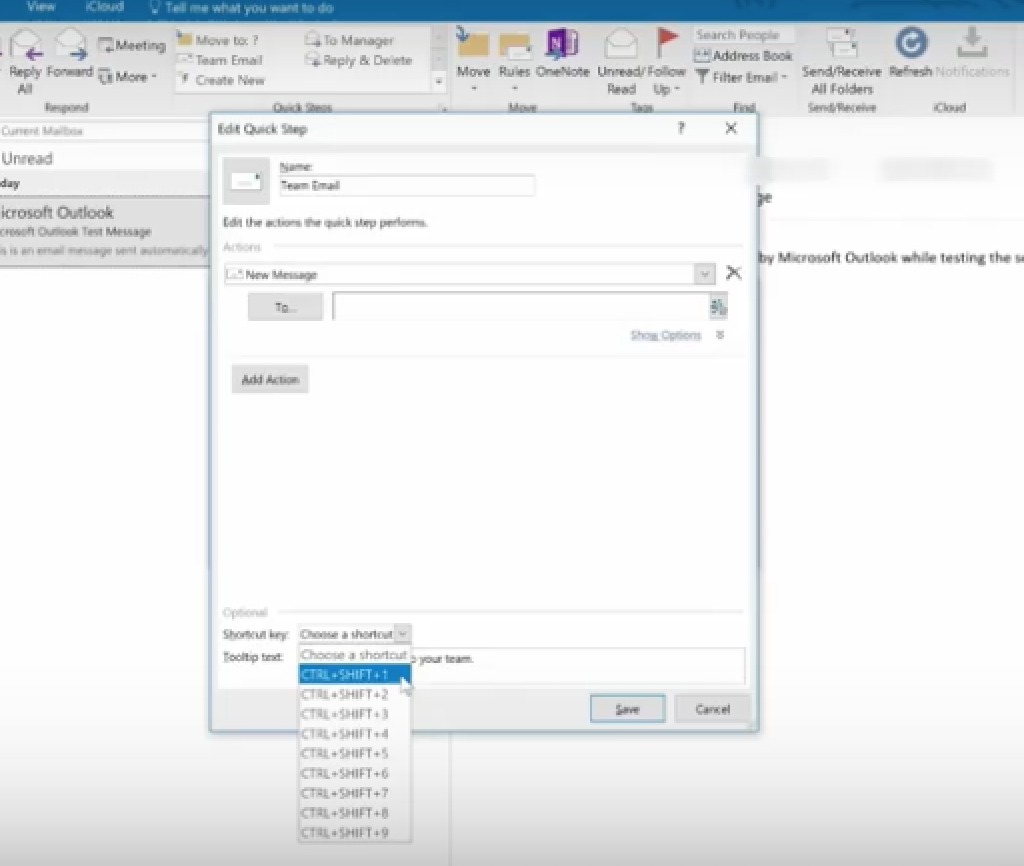
You can also create new Quick Step. Simply choose Create New Quick Step.
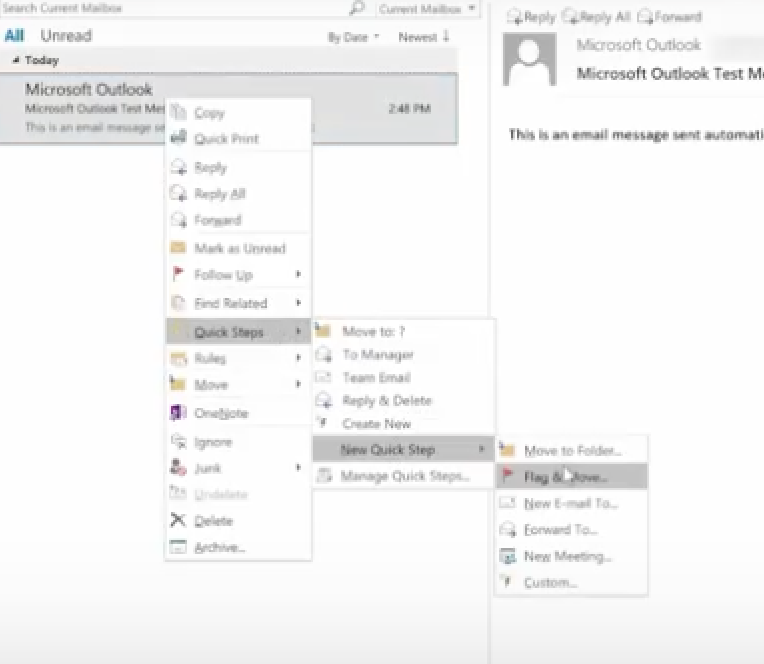
Here are some other Quick Steps to try: 1
- Move to Folder: This is essentially the same as Move To.
- Categorize & Move: This moves the selected message to a specific folder, marks the message as read, and assigns a category color and name to the message.
- Flag & Move: This moves the selected message to a specific folder, marks the message as read, and assigns a flag to the message.
- New Email To: This opens a New Message form with the To field already filled out with a particular recipient.
- Forward To: This is essentially the same as To Manager.
- New Meeting: If you often send meeting invites to the same group of people, use this Quick Step to open a New Meeting form with the To field already filled in with the invitees.
- Custom: This opens the Edit Quick Step dialog box so that you can create your own custom Quick Step.
3. Use Conditional Formatting
This is used to change the look of a particular email. You do this in the View Menu.
Here, we just click on Conditional Formatting and create an email called Microsoft.
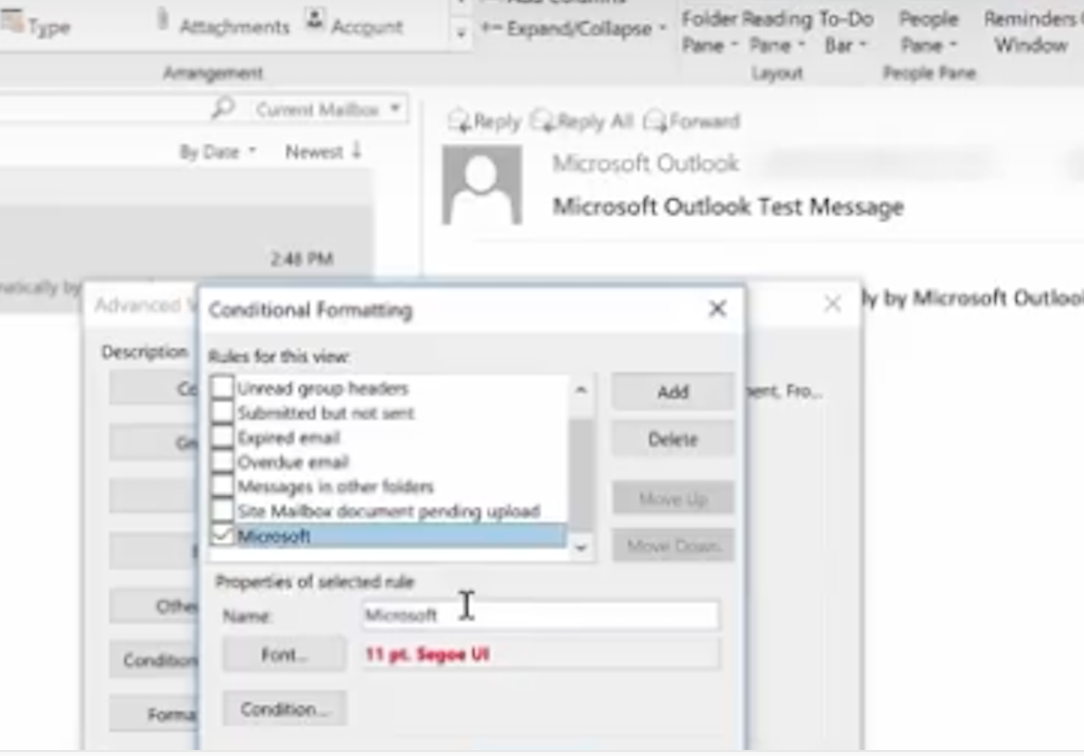
Next, we choose a condition, where the word Microsoft appears anywhere in an email.
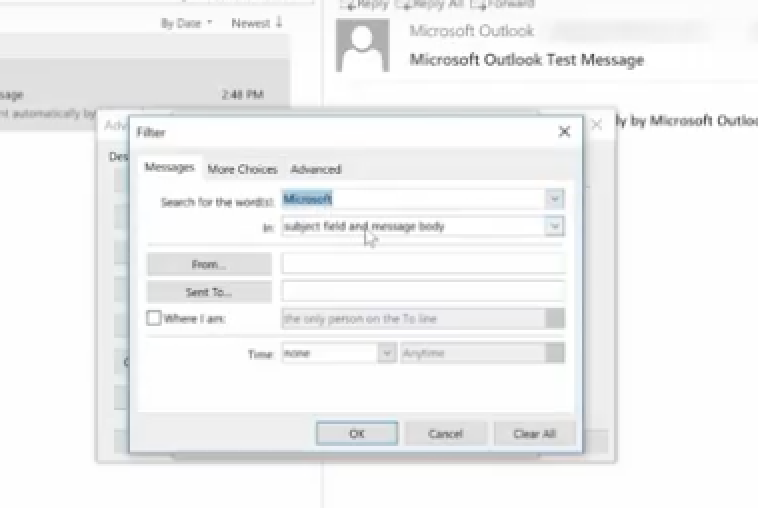
Then, we ask it to appear in a bold red font.
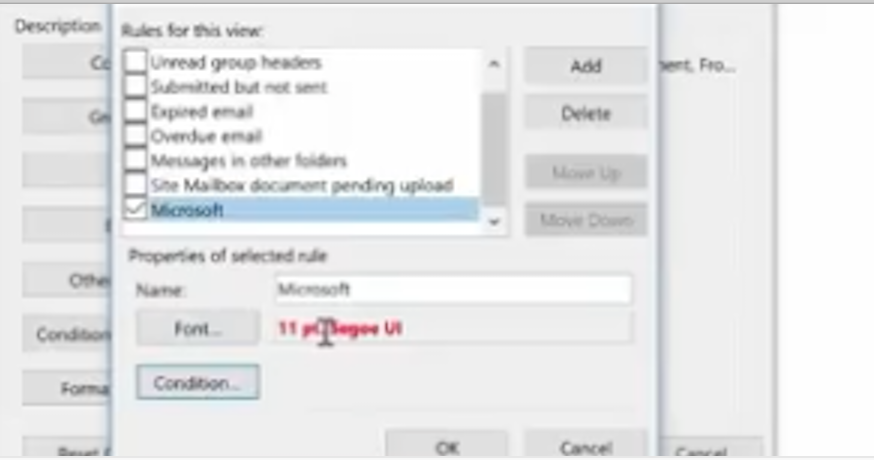
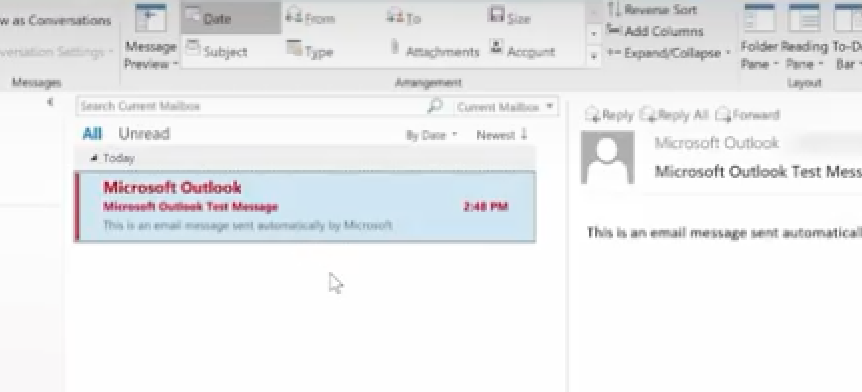
Now, any new email we receive with the word Microsoft in it will show up in red. This is a great way for us to recognize the importance of an email. You may want to do this for any email with your boss’s name in it!
And, there are more ways you can get the most from Outlook 2016. Here are a few ideas:
- Change the color and contrast of Outlook: You can also use a picture or color as the background, add a text watermark to your emails.
- Customize emails with the fonts you prefer: Change the default font for various email messages you send, or a particular font for messages that you forward or reply to.
- Create signatures for your different email accounts: Create personalized signatures for your email messages: include text, images, your electronic business card, a logo, or even an image of your handwritten signature. Signatures can be added automatically to all outgoing messages, or you can choose which messages should use a particular signature.
- Setup sound alerts when new emails come in: A sound can play when a new email message arrives. The default sound is a short .wav audio file, but you can change it to any .wav file of your choice.
- Establish tracking options with delivery receipts: A delivery receipt confirms delivery of your email message to the recipient’s mailbox.
- Use Outlook’s templates for your messages or create your own: Use email templates to send messages that include information that rarely changes from message to message. You can also insert icons, photos, and tables into your messages.
- Embed voting buttons in your email to survey your recipients about a particular topic (such as, “When’s the best date and time for a meeting?”): Voting buttons are an excellent way to poll people, especially when communicating with large groups.
- Use Quickparts to insert a standard set of words you often use: Use the Quick Parts Gallery to create, store, and locate content, including AutoText, document properties such as title and author, and fields.
- Clutter: This is where you can place low priority emails you want to read later. Clutter helps you filter these low-priority emails saving time for your most important messages. Office 2016 remembers “Clutter” emails if you want. If Clutter isn’t for you, you can TURN IT OFF.
- Create folders and subfolders: You can base these on topics, senders, organizations, projects, etc.—Whatever works for you and organize your emails under the subjects you choose. Use folders in Outlook to move email messages, add a folder to your Favorites, and set a rule to move specific emails out of your inbox.
CALENDAR
Outlook 2016 calendars have all the tools and functionality you’ve relied on in the past, with improved features to help you manage your time.
- Set up multiple calendars (e.g., personal, business, health, etc.).
- Create appointments quickly and share them with your contacts.
- Scheduling assistant lets you access others’ calendars that you’re authorized to view (and vice versa).
- Set reminders, reoccurring appointments/meetings, alerts, and more.
- View your calendar by day, week, month, and year.
CONTACTS
- You can also import contacts to Outlook from other email providers using the Outlook Import/Export wizard. Import a CSV file, Excel spreadsheet, or vCard.
- Your contacts are linked to your email accounts, so you can simply key a name in the “To” field, and your contact’s email address will appear.
- Set permission for a particular contact (delegate) to view your emails while you’re on vacation. Plus, you can give this person access to your calendar, tasks, and so on, as appropriate. One delegate can take care of your email, another your tasks, etc.
TOOLS
- Always know how much space is left in your account.
- Notify those emailing you that you aren’t available during a particular period with Out of Office. You set up a special message you want others to see.
- Even set up different messages for people inside or outside your organization. (Outlook will remind you that the “Out of Office” message is turned on, so you don’t forget when you return.)
- As mentioned above, similar to having an assistant help you manage your incoming paper mail, you can use Microsoft Outlook to allow a delegate, to receive and respond to e-mail messages and meeting requests and responses on your behalf.
- You can also grant additional permissions that allow your delegate to read, create, or have more control over items in your Microsoft Exchange Server mailbox—And, set more than one delegate and permissions for various tasks.
TASKS
Outlook 2016’s task management helps you accomplish to-dos faster and easier.
- Categorize your tasks with color codes.
- Ping reminders for tasks.
- Check-off tasks when complete.
- Create tasks for others as well. Outlook integrates tasks with your emails so that you can assign a task to a recipient. The task will show up on their task list.
To learn more about how you can get the most from Outlook 2016 contact us.