Phishing Scams: How to Recognize and Avoid Them
What Are Phishing Scams? Phishing scams are deceptive attempts by cybercriminals to steal your sensitive information, such as usernames, passwords,...
Read More
5 Advantages of Our Strategic Business Reviews
Our mission is to be more than just your IT support provider—we aim to be your trusted partner in growth....
Read More
Enhance Account Security with Multi-Factor Authentication (MFA)
What is Multi-Factor Authentication (MFA)? Multi-Factor Authentication, or MFA, adds an extra layer of security to your accounts by requiring...
Read More
Secure Password Management
Strong and secure password management is more critical than ever for safeguarding sensitive business data. Implementing a password manager such...
Read More
The New Outlook
Overview of the New Outlook for Windows Welcome to the era of enhanced productivity and streamlined communication with the new...
Read More
Our Commitment to our Community
At Infinet Solutions, our commitment to giving back is as strong as our passion for technology and business. Through our...
Read More
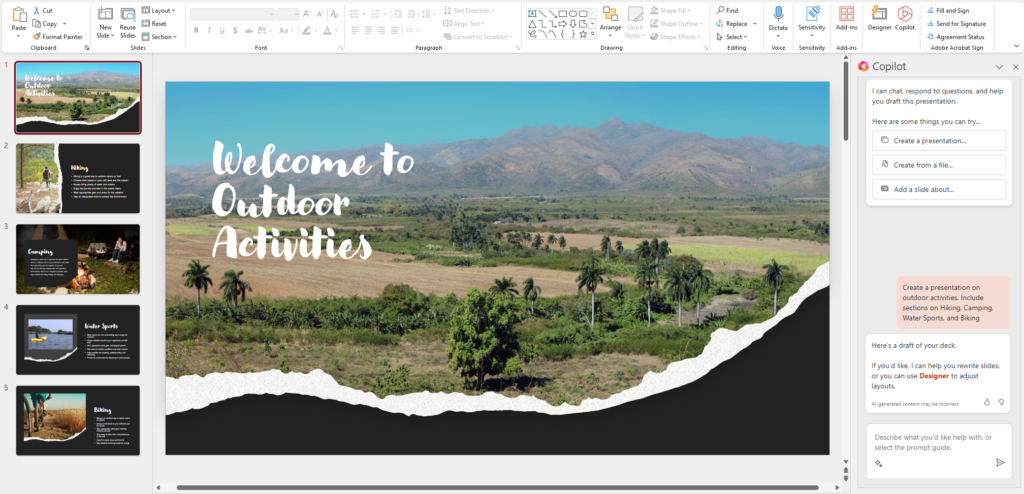
Making PowerPoint presentations with Copilot
Copilot helps you summarize long email threads, view different perspectives, and identify unanswered questions. You can quickly respond using prompts...
Read More
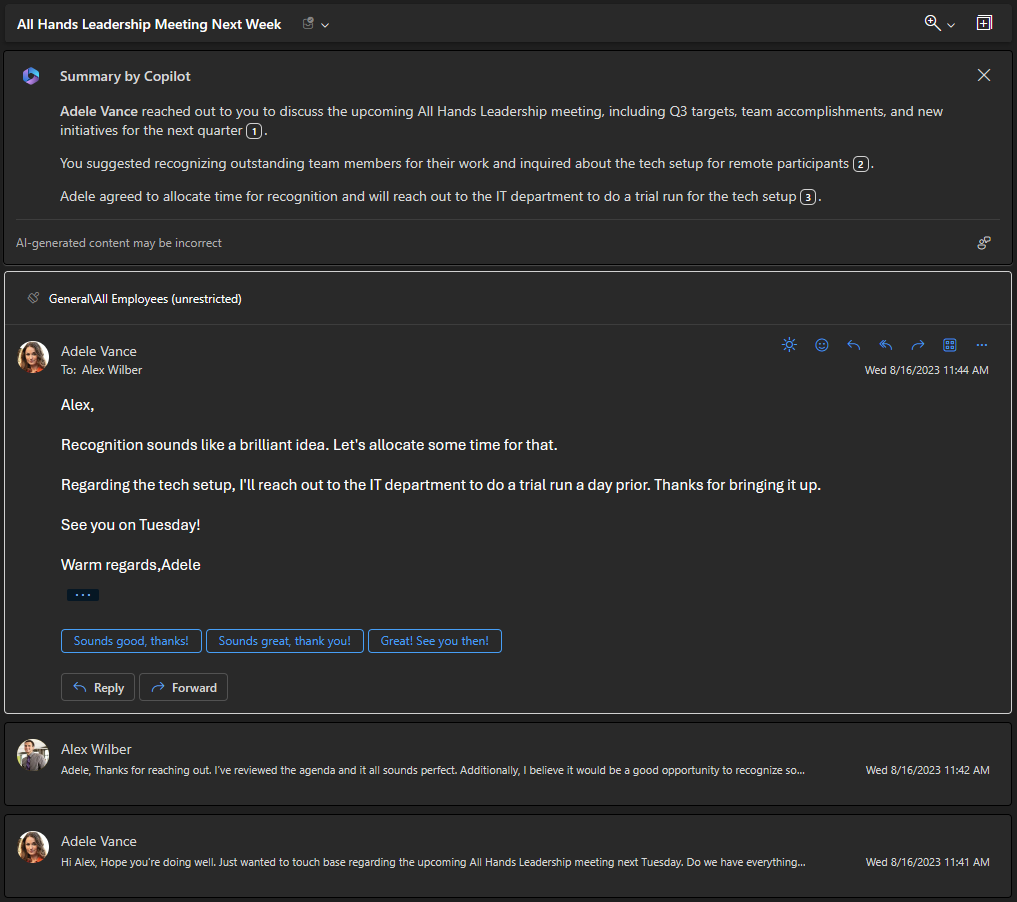
Microsoft Copilot Series: Summarize and draft emails with Copilot
Copilot helps you summarize long email threads, view different perspectives, and identify unanswered questions. You can quickly respond using prompts...
Read More
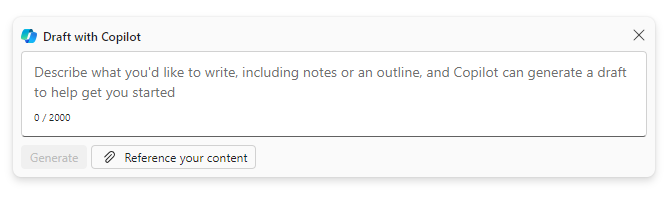
Microsoft Copilot Series: How to use Copilot in Word
In Word, Copilot for Microsoft 365 revolutionizes the way you create and refine documents, making it easier than ever to...
Read More
Onsite and Remote IT Support Omaha
Feeling a bit overwhelmed by your IT challenges? Well, fret not, because Infinet Solutions is here to sprinkle some IT...
Read More
Top 5 Benefits of Using Cloud Services
Welcome to the dynamic world of cloud computing, a game-changer for small businesses seeking to punch above their weight in...
Read More
Cybersecurity: What is credential stuffing?
https://youtu.be/mUb0GaprAOs
Read More
Remote Workforces Deliver Business & Employee Benefits
When considering the employee and employer benefits of working remotely, businesses are wise to change. The alternative could make your...
Read More
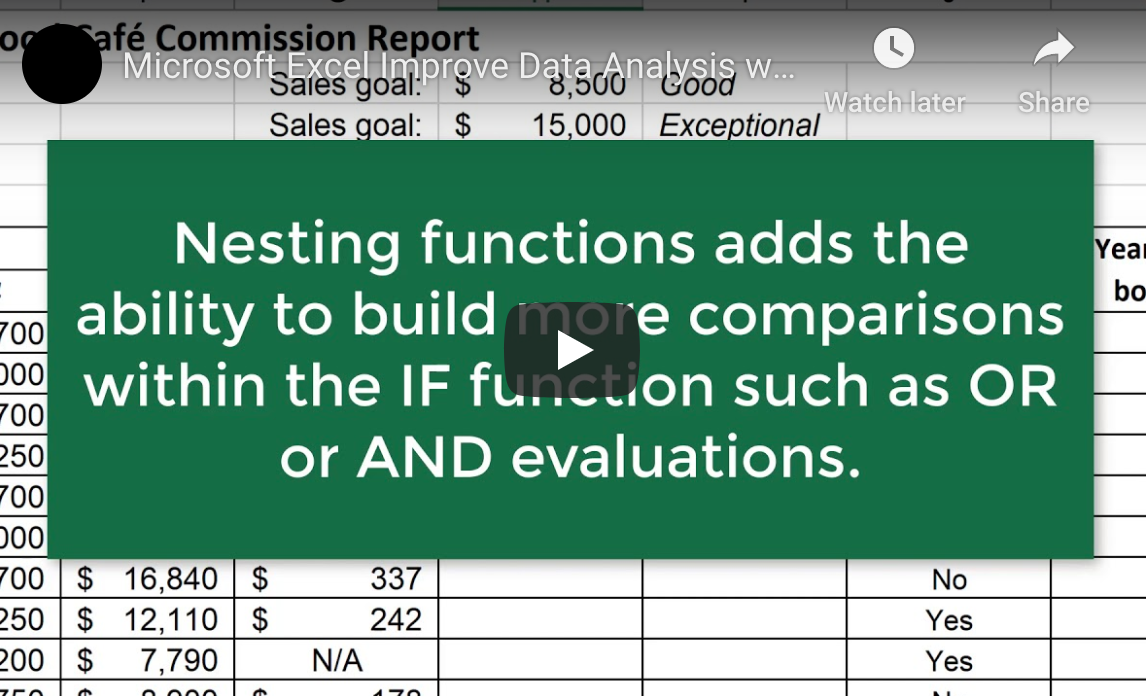
Top Tips for Improving Data Analysis with the IF Function in Microsoft Excel
Improving Data Analysis with the IF Function in Microsoft Excel Have you ever wondered what the IF Function in Microsoft...
Read More
Know the Digital Threats: 6 Dangerous Malware & How to Stop Them
Know and Protect Your Network From These Malware Threats Every day, new malware is discovered that threatens U.S. business and...
Read More
Use SharePoint to Keep Business Data Organized
Metadata Gives You Control of Disorganized Online Filing Systems SharePoint gives you a simple solution to keep your online files...
Read More
Ransomware Explained…
Ransomware is a form of malware that encrypts your files and demands a ransom payment in exchange for the decryption...
Read More
7 Myths Small Businesses Still Believe About PC Technology
The 7 PC Myths Draining Your Business Technology Budget Evaluating your business technology budget? These 7 PC myths could be...
Read More
What You Need to Know about Cyber Security
Cybersecurity education is essential in order to keep businesses one step ahead of this evolving space. Learn about types of...
Read More
Keeping You Safe from Juice Jacking
Learn about juice jacking and how to prevent you or employees from becoming a victim. Here’s a new cyber threat...
Read More